Software Iam
Stop Guessing Passwords: Why Robust Software Iam Is Your Security MVP
If you're managing a growing business or even a large enterprise, you know the security landscape is less like a solid castle and more like shifting sand. We rely on countless cloud services, hundreds of applications, and a workforce that might be anywhere in the world.
In this decentralized digital reality, the old perimeter defense model is dead. The new perimeter is the identity of the user. That's where robust **Software Iam** (Identity and Access Management) steps in. It's not just an IT tool; it's the crucial backbone that determines who gets access to what, when, and how.
In this deep dive, we'll move beyond the buzzwords. We'll explore what makes a great IAM solution, why neglecting this area leads to massive security headaches, and how to choose the right platform that aligns with modern security frameworks like Zero Trust.
What Exactly Is Identity and Access Management (IAM) Software?
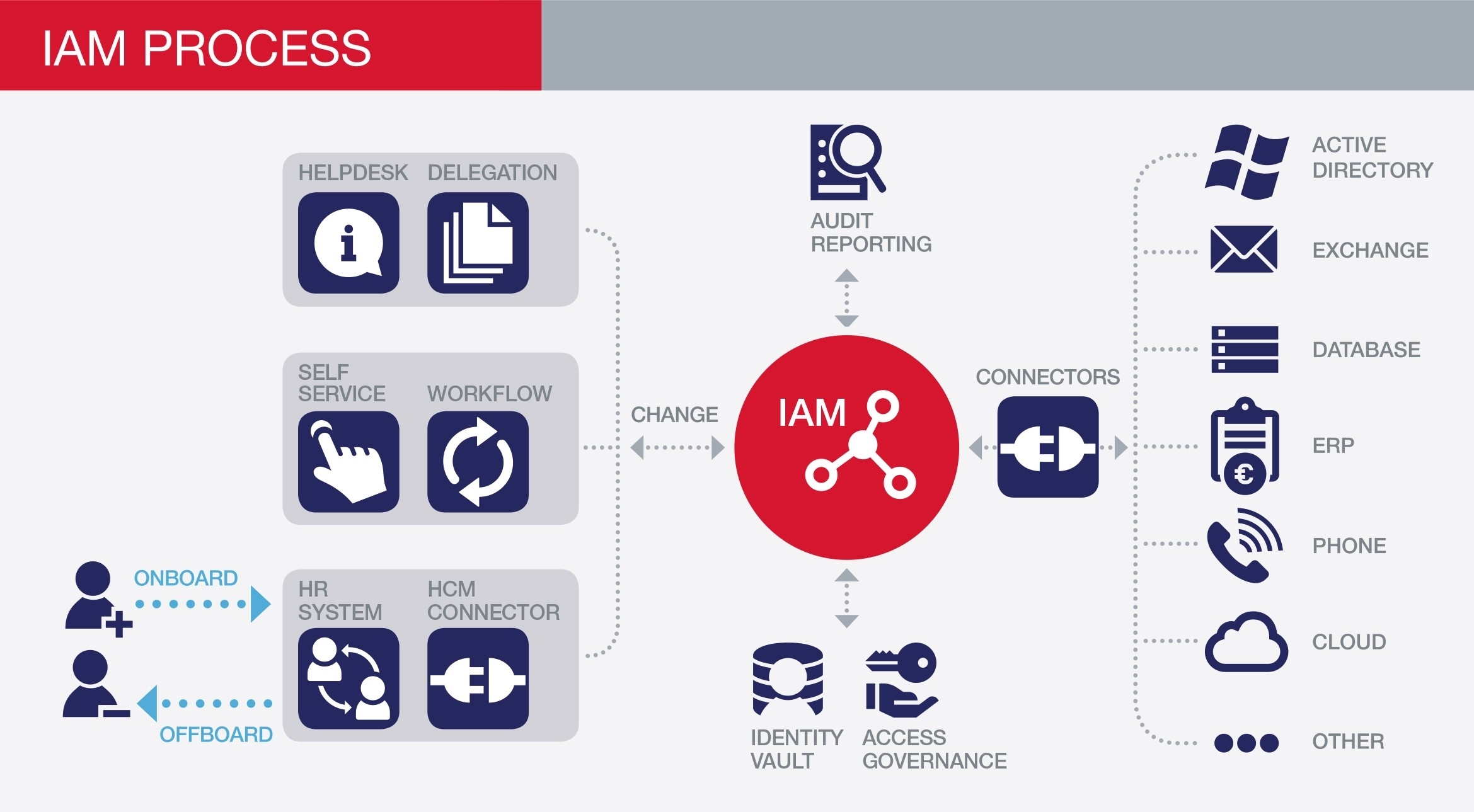
At its core, IAM software is a framework of policies and technologies designed to manage digital identities and control how those identities interact with corporate resources. Think of it as the ultimate bouncer, receptionist, and auditor rolled into one system.
The goal is deceptively simple: ensure that the right people and the right devices have access to the right resources at the right time—and nothing more. This eliminates the risk of excessive permissions, which is a leading cause of data breaches.
The Four Key Pillars of Modern IAM
A comprehensive IAM solution typically handles four major areas:
- Authentication: Verifying the identity (e.g., passwords, Multi-Factor Authentication/MFA, biometrics).
- Authorization: Determining what the verified identity is allowed to do (e.g., read-only, edit, delete).
- User Lifecycle Management: Creating, maintaining, and eventually de-provisioning user accounts swiftly when employees join or leave.
- Auditing and Compliance: Tracking and reporting all access events to satisfy regulatory requirements like GDPR, HIPAA, or ISO 27001.
If your current system involves manually resetting passwords via email and spreadsheet tracking of user permissions, you are severely overdue for implementing robust **Software Iam**.
Why Software Iam Is Now Non-Negotiable
The transition to cloud computing and remote work (often called the "de-perimeterization" of the network) means traditional security tools are less effective. Attackers no longer need to breach a physical firewall; they just need one weak credential.
Meeting the Zero Trust Mandate
The concept of "Never Trust, Always Verify" is the driving force behind modern security architectures, formalized by organizations like NIST. IAM software is the engine that powers this architecture.
Zero Trust requires continuous verification based on context (user, location, device health) before granting access, no matter where the user is located or what resource they are trying to reach. Without sophisticated IAM tools, achieving a true Zero Trust model is impossible. The NIST Zero Trust Model emphasizes identity as the core policy enforcement point.
The Cost of Credential Compromise
Data consistently shows that credential compromise is the root cause of the vast majority of successful breaches. When you automate access controls using IAM, you drastically reduce the attack surface area and dramatically improve your regulatory standing.
A unified IAM system streamlines operations, reduces helpdesk calls for password resets, and ensures that former employees or contractors lose access instantaneously, reducing insider threat risks.
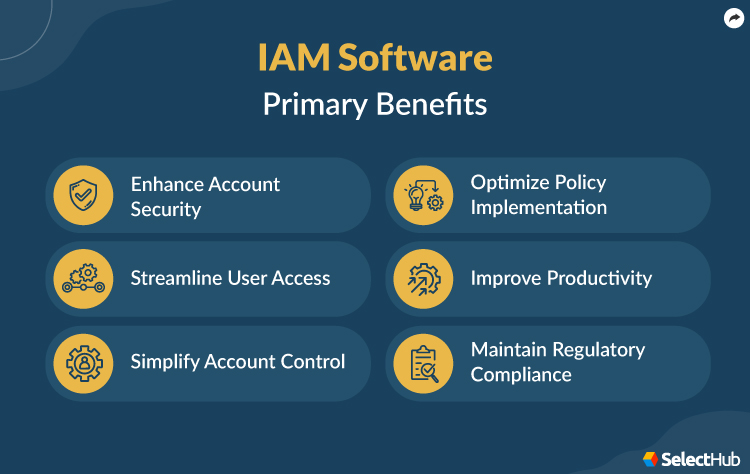
The Core Pillars: Features to Look for in IAM Solutions
When evaluating which **Software Iam** solution is right for your organization, look for platforms that seamlessly integrate the following critical features:
1. Single Sign-On (SSO)
SSO allows users to log in once with one set of credentials and gain access to multiple applications (SaaS, internal apps, cloud services) without re-authenticating. This improves user experience and dramatically reduces "password fatigue," leading users away from weak or reused passwords.
2. Multi-Factor Authentication (MFA)
MFA requires users to present two or more verification factors (e.g., something they know—password; something they have—phone/token; something they are—fingerprint). This is widely considered the single most effective defense against credential theft.
3. Privileged Access Management (PAM)
This critical function focuses specifically on high-value accounts (system administrators, database managers) that have broad, powerful access. PAM solutions monitor and control sessions, ensuring that "super-users" only use their elevated privileges when absolutely necessary. [Baca Juga: MFA Best Practices]
4. Adaptive and Contextual Access Policies
The best IAM software doesn't just check the password; it continuously evaluates the context. Is the user logging in from a new country? Are they using a non-compliant device? Adaptive policies automatically step up authentication requirements or block access based on this risk assessment.
Cloud vs. On-Premise: Choosing Your Deployment Strategy
The decision between hosting your IAM solution in your own data center (On-Premise) or relying on a vendor's service (Cloud/IDaaS - Identity as a Service) depends heavily on your existing infrastructure, budget, and compliance needs. While On-Premise offers maximum control, Cloud solutions dominate the modern market due to speed and scalability.
Here's a quick comparison to help you assess the trade-offs:
| Feature | Cloud IAM (IDaaS) | On-Premise IAM |
|---|---|---|
| Initial Setup Cost | Low (Subscription-based) | High (Hardware/Licensing) |
| Scalability | Excellent; handles large user fluctuations easily. | Limited; requires hardware upgrades. |
| Maintenance & Updates | Handled by the vendor (automatic). | Managed entirely by internal IT staff. |
| Compliance Suitability | Very high for most global standards. | Best for highly regulated environments needing isolated data centers. |
For most modern companies, the flexibility and lower operational overhead of Cloud IAM make it the preferred choice for managing identity in the age of SaaS applications and hybrid workforces. You can read more about the evolution of IAM here.
Navigating the Market: Key Players and Trends
The IAM market is crowded and competitive. The major players—like Okta, Microsoft Azure AD (Entra ID), Ping Identity, and CyberArk (especially for PAM)—each offer compelling feature sets. Your choice should depend on your ecosystem.
Integration is King
If you are heavily invested in the Microsoft ecosystem, Azure AD is often a natural fit. If you prioritize vendor neutrality and integration with thousands of external SaaS applications, a standalone IDaaS platform might be superior. Always check the vendor's integration catalog before committing.
The Rise of CIAM (Customer IAM)
Beyond managing internal employees (Workforce IAM), there is a massive trend toward CIAM. This focuses on managing millions of customer identities securely and at scale, ensuring smooth customer journeys while protecting personal data. [Baca Juga: Zero Trust Architecture]
Ultimately, the best Software Iam solution is the one that minimizes friction for authorized users while maximizing the defense against malicious actors. It's a balance of security and usability—a delicate act that modern platforms are constantly trying to perfect. External analysis on current market leaders can be helpful.
Conclusion: Identity as the New Core Defense
In the end, cybersecurity is no longer about firewalls and antivirus alone; it is fundamentally about identity. A strong **Software Iam** strategy moves your organization away from reactive defense and toward a proactive, identity-centric security posture.
By implementing robust SSO, strong MFA, and contextual access policies, you protect your most valuable assets, ensure regulatory compliance, and provide a seamless, secure experience for every user, wherever they work.
Frequently Asked Questions (FAQ) About IAM Software
- What is the difference between IAM and PAM?
IAM (Identity and Access Management) manages all user identities (employees, contractors, customers). PAM (Privileged Access Management) is a specialized subset of IAM focused solely on high-risk, high-power "privileged" accounts (like system admins) that have critical access to infrastructure.
- Can I use only MFA and skip the full IAM software suite?
MFA is essential, but it only handles authentication (Step 1). A full IAM suite manages authorization, lifecycle provisioning, and detailed auditing required for compliance and enterprise-level risk reduction. MFA is a tactic; IAM is the overall strategy.
- How long does it take to implement enterprise-grade IAM software?
Implementation time varies greatly based on complexity. A cloud-based SSO rollout might take a few weeks, but a full-scale migration covering thousands of users, integrating complex legacy applications, and implementing PAM can take 6 to 12 months, requiring careful planning and staged deployment.
- What is the biggest challenge when adopting new IAM software?
The biggest challenge is usually integration with legacy systems. Older, proprietary applications often lack support for modern identity protocols (like SAML or OIDC), requiring custom connectors or application modernization, which can increase project costs and timelines.
Software Iam
Software Iam Wallpapers
Collection of software iam wallpapers for your desktop and mobile devices.

Dynamic Software Iam Capture Photography
Immerse yourself in the stunning details of this beautiful software iam wallpaper, designed for a captivating visual experience.

Beautiful Software Iam View for Mobile
Explore this high-quality software iam image, perfect for enhancing your desktop or mobile wallpaper.

Spectacular Software Iam View Collection
This gorgeous software iam photo offers a breathtaking view, making it a perfect choice for your next wallpaper.

Beautiful Software Iam Wallpaper Concept
Explore this high-quality software iam image, perfect for enhancing your desktop or mobile wallpaper.

Captivating Software Iam Design Concept
Immerse yourself in the stunning details of this beautiful software iam wallpaper, designed for a captivating visual experience.

Captivating Software Iam Artwork Concept
This gorgeous software iam photo offers a breathtaking view, making it a perfect choice for your next wallpaper.
Dynamic Software Iam Wallpaper Nature
A captivating software iam scene that brings tranquility and beauty to any device.

Amazing Software Iam Wallpaper Art
Discover an amazing software iam background image, ideal for personalizing your devices with vibrant colors and intricate designs.

Vibrant Software Iam Landscape Concept
Explore this high-quality software iam image, perfect for enhancing your desktop or mobile wallpaper.

Captivating Software Iam Abstract Illustration
A captivating software iam scene that brings tranquility and beauty to any device.

Mesmerizing Software Iam Capture for Your Screen
Transform your screen with this vivid software iam artwork, a true masterpiece of digital design.
Breathtaking Software Iam Wallpaper in 4K
Transform your screen with this vivid software iam artwork, a true masterpiece of digital design.

Amazing Software Iam Artwork Collection
Transform your screen with this vivid software iam artwork, a true masterpiece of digital design.

High-Quality Software Iam View Illustration
Discover an amazing software iam background image, ideal for personalizing your devices with vibrant colors and intricate designs.

Mesmerizing Software Iam Scene Art
Discover an amazing software iam background image, ideal for personalizing your devices with vibrant colors and intricate designs.
Vibrant Software Iam Artwork Art
Experience the crisp clarity of this stunning software iam image, available in high resolution for all your screens.
Stunning Software Iam Abstract Photography
Immerse yourself in the stunning details of this beautiful software iam wallpaper, designed for a captivating visual experience.

Vibrant Software Iam Artwork in HD
Transform your screen with this vivid software iam artwork, a true masterpiece of digital design.

Mesmerizing Software Iam Artwork for Mobile
Transform your screen with this vivid software iam artwork, a true masterpiece of digital design.

High-Quality Software Iam View Digital Art
Discover an amazing software iam background image, ideal for personalizing your devices with vibrant colors and intricate designs.
Download these software iam wallpapers for free and use them on your desktop or mobile devices.
0 Response to "Software Iam"
Post a Comment