Endpoint Detection And Response Software
Your Old Antivirus Is Not Enough: Why You Urgently Need Endpoint Detection And Response Software
If you still rely solely on traditional antivirus (AV) software to protect your business, you might be driving a Model T on a Formula 1 track. It might get you from point A to point B, but you're highly vulnerable to everything else speeding past you.
The cybersecurity landscape has changed dramatically. Modern threats—like fileless malware, sophisticated ransomware, and zero-day exploits—are designed specifically to bypass old, signature-based defenses.
This is where the power of modern cybersecurity steps in: the Endpoint Detection And Response Software, or EDR. EDR doesn't just block known viruses; it watches, learns, and reacts to suspicious behavior in real-time across all your critical endpoints.
Ready to upgrade your defenses? Let's dive deep into what EDR is, why it's essential, and how it delivers true resilience against today's most dangerous attacks.
What Exactly is Endpoint Detection And Response Software (EDR)?
At its heart, EDR is a security solution that continuously monitors and records all activity on your endpoints (laptops, servers, mobile devices) to quickly detect, investigate, and mitigate advanced threats.
Think of traditional AV as a security guard who only recognizes 10 known criminals by their photo. EDR, however, is a full surveillance team that monitors every person's behavior, instantly flagging anyone who looks suspicious, regardless of whether they have a "wanted" poster.
According to Gartner, which coined the term, EDR focuses on four key capabilities: security incident detection, containment, investigation, and eradication.
EDR vs. Traditional Antivirus: The Key Difference
The distinction lies primarily in their approach to threats:
- Traditional AV: Relies on signatures (known files/viruses). If a brand-new threat emerges, the AV is blind until its database is updated. It's a reactive "prevent-only" tool.
- EDR Software: Utilizes behavioral analysis, machine learning (ML), and threat intelligence. It doesn't need to know the specific virus file; it just needs to recognize anomalous behavior—like a legitimate process suddenly trying to encrypt thousands of files (the hallmark of ransomware).
This proactive stance allows EDR to catch threats that "live off the land"—using built-in operating system tools—which are notoriously difficult for older AV tools to spot.
[Baca Juga: Memahami Perbedaan Antara EDR dan Next-Generation Antivirus (NGAV)]
The Core Pillars of Modern Endpoint Detection And Response Software
For EDR to be truly effective, it must excel in three core areas:
Detection and Alerting
Modern EDR tools use complex algorithms to analyze massive volumes of telemetry data (logs, file execution, network connections). It doesn't just alert you to a problem; it provides context.
Instead of receiving 1,000 separate alerts about blocked connections, the EDR platform stitches them together into one high-priority "incident" timeline, allowing security teams to see the full scope of an attack immediately.
Investigation and Threat Hunting
This is where EDR shines brightest compared to traditional tools. EDR maintains a historical record of all endpoint activity, allowing analysts to "rewind" time.
If a new vulnerability is discovered today, security teams can use the EDR data lake to retroactively check if that vulnerability was exploited months ago. This process, known as Threat Hunting, turns passive defense into active pursuit.
For more detailed reading on forensic readiness and cyber security incident handling, you can consult sources like NIST Special Publication 800-61.
Containment and Remediation
Once a threat is identified, speed is paramount. EDR allows security teams (or automated responses) to immediately quarantine the affected endpoint, isolating it from the rest of the network to prevent lateral movement.
Remediation often involves automatically terminating malicious processes, removing persistent files, and reverting the endpoint to a clean state, minimizing dwell time and recovery efforts.
Choosing the Right Endpoint Detection And Response Software for Your Business
Selecting EDR isn't just about features; it's about fitting the solution to your team's capability and capacity.
Key Considerations for EDR Selection:
- Visibility & Coverage: Does it support all your operating systems (Windows, macOS, Linux) and cloud environments?
- Ease of Use: Is the console intuitive? If your team spends too much time navigating complex dashboards, response times suffer.
- Integration: Does it integrate smoothly with other security tools you already use, such as SIEM or firewall solutions?
- Performance Overhead: Does the EDR agent heavily slow down the endpoint device? A sluggish device frustrates users and impacts productivity.
Managed Detection and Response (MDR) Considerations
Many organizations realize they lack the 24/7 staffing or deep expertise required to manage EDR effectively. EDR tools generate a lot of data, and someone needs to analyze it constantly.
If this describes your organization, consider an EDR solution paired with a Managed Detection and Response (MDR) service. MDR partners take the heavy lifting off your hands, providing human threat hunters and incident responders around the clock.
EDR in Action: Real-World Benefits
The practical benefits of deploying sophisticated Endpoint Detection And Response Software are tangible and directly impact business continuity:
1. Stopping Fileless Attacks
Fileless attacks use scripts and memory to execute their malicious payloads without dropping a file to disk. Since there is no signature to scan, traditional AV fails. EDR monitors process behavior, catches the suspicious script execution in memory, and immediately shuts it down.
2. Better Regulatory Compliance
Many regulations (like GDPR, HIPAA, and CCPA) require organizations to demonstrate robust security controls and the ability to investigate breaches thoroughly. EDR's centralized data collection provides the necessary forensic evidence trail for compliance reporting.
You can find an authoritative overview of global regulatory standards on the ISO/IEC 27001 standard for information security management.
[Baca Juga: Strategi Pencegahan Data Loss (DLP) yang Terintegrasi dengan EDR]
Comparison: EDR Capabilities vs. Traditional AV
To summarize why the switch is crucial, here is a quick comparison:
| Feature | Traditional Antivirus | Endpoint Detection And Response (EDR) |
|---|---|---|
| Detection Method | Signature-based, Known Threats Only | Behavioral Analysis, AI/ML, Threat Intelligence |
| Visibility Scope | Limited to Malware Scanning | Full Logging of All Endpoint Activity |
| Response Capability | Quarantine/Delete File | Rollback, Isolate Network, Terminate Process Chain |
| Threat Hunting | No | Yes (Historical Data Analysis) |
Conclusion: EDR is Resilience, Not Just Prevention
In the digital age, it's no longer a question of *if* your organization will face an attack, but *when*. The role of the Endpoint Detection And Response Software is not just to prevent the inevitable but to ensure you have the resilience to minimize damage when a breach occurs.
By moving beyond outdated defenses and embracing EDR, you empower your security team with the depth, context, and automated response capabilities necessary to compete—and win—against today's most sophisticated adversaries.
Frequently Asked Questions About EDR
- Is EDR the same as NGAV (Next-Generation Antivirus)?
No, but they work together. NGAV focuses on preventive measures using AI/ML instead of signatures. EDR includes NGAV functionality but adds the crucial layers of monitoring, investigation, and incident response. EDR is the broader solution.
- Does EDR slow down my computer?
Modern EDR agents are designed to be extremely lightweight, utilizing cloud-based processing power to minimize the impact on the local endpoint CPU and memory. However, performance can vary between vendors, so testing is recommended.
- Who typically needs Endpoint Detection And Response Software?
While often mandatory for large enterprises with complex environments, EDR is increasingly critical for SMEs (Small and Medium Enterprises) that handle sensitive customer data, especially those targeted by fileless attacks and ransomware. Any organization with high-value digital assets should consider EDR.
- How long does EDR keep the endpoint data?
This is vendor-dependent and based on licensing and compliance needs. Most EDR solutions store historical telemetry data in the cloud for anywhere from 30 days to a year or more, enabling long-term threat hunting and forensic analysis.
Endpoint Detection And Response Software
Endpoint Detection And Response Software Wallpapers
Collection of endpoint detection and response software wallpapers for your desktop and mobile devices.

Dynamic Endpoint Detection And Response Software Image for Your Screen
This gorgeous endpoint detection and response software photo offers a breathtaking view, making it a perfect choice for your next wallpaper.
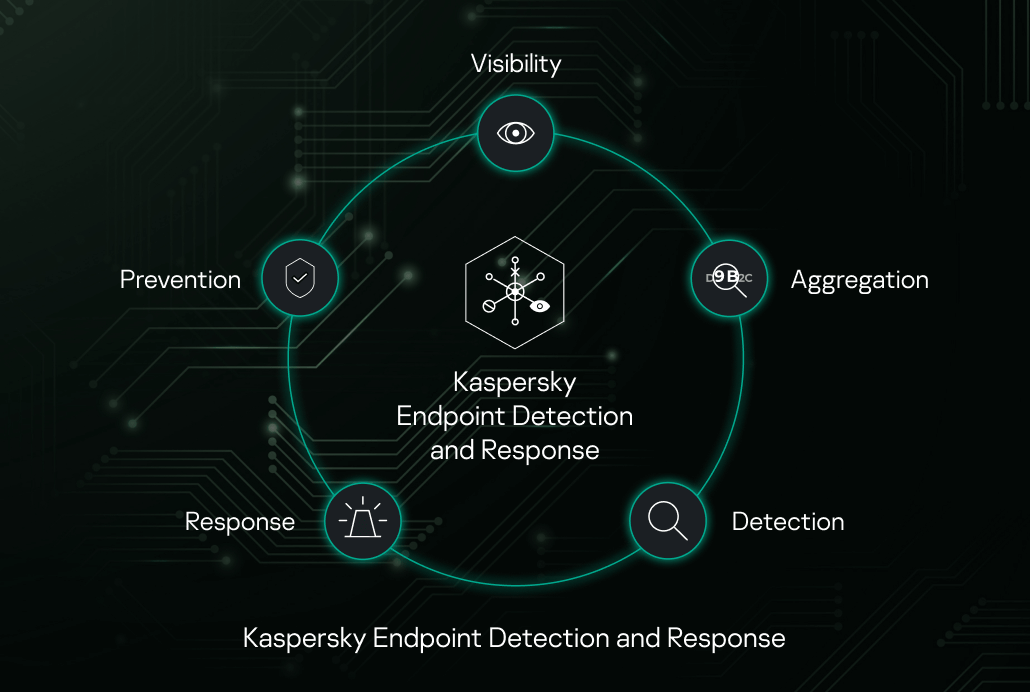
Captivating Endpoint Detection And Response Software Photo for Desktop
This gorgeous endpoint detection and response software photo offers a breathtaking view, making it a perfect choice for your next wallpaper.

Breathtaking Endpoint Detection And Response Software Capture Art
Experience the crisp clarity of this stunning endpoint detection and response software image, available in high resolution for all your screens.

Mesmerizing Endpoint Detection And Response Software View Collection
Explore this high-quality endpoint detection and response software image, perfect for enhancing your desktop or mobile wallpaper.

Beautiful Endpoint Detection And Response Software Photo for Mobile
Transform your screen with this vivid endpoint detection and response software artwork, a true masterpiece of digital design.

High-Quality Endpoint Detection And Response Software Background in 4K
Discover an amazing endpoint detection and response software background image, ideal for personalizing your devices with vibrant colors and intricate designs.

Lush Endpoint Detection And Response Software Capture for Mobile
A captivating endpoint detection and response software scene that brings tranquility and beauty to any device.

Captivating Endpoint Detection And Response Software Scene for Desktop
Find inspiration with this unique endpoint detection and response software illustration, crafted to provide a fresh look for your background.
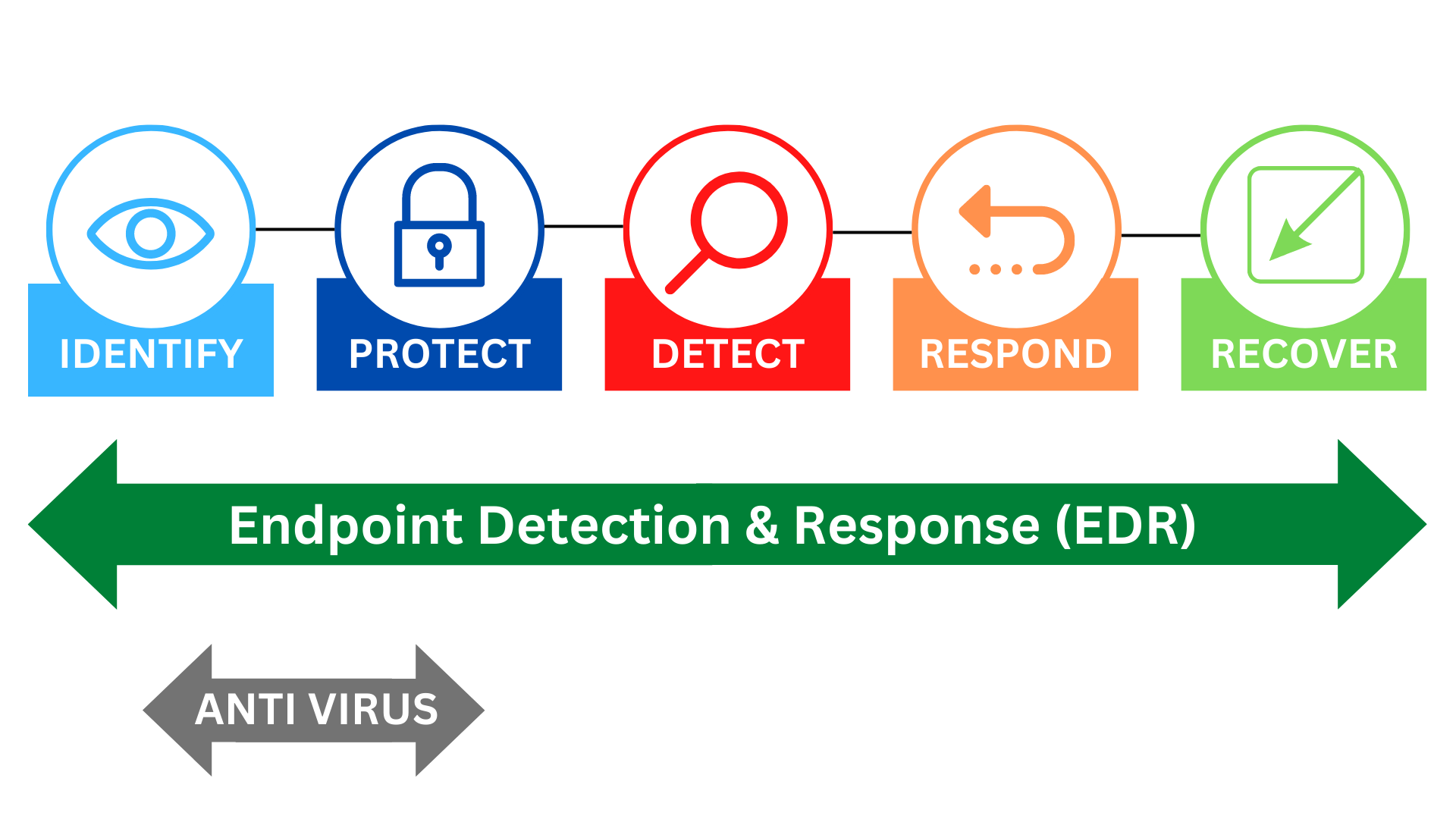
Gorgeous Endpoint Detection And Response Software Moment for Mobile
This gorgeous endpoint detection and response software photo offers a breathtaking view, making it a perfect choice for your next wallpaper.

Artistic Endpoint Detection And Response Software Picture in HD
This gorgeous endpoint detection and response software photo offers a breathtaking view, making it a perfect choice for your next wallpaper.

Captivating Endpoint Detection And Response Software Background for Mobile
A captivating endpoint detection and response software scene that brings tranquility and beauty to any device.

Lush Endpoint Detection And Response Software Scene Nature
Find inspiration with this unique endpoint detection and response software illustration, crafted to provide a fresh look for your background.

Vivid Endpoint Detection And Response Software Wallpaper Art
Experience the crisp clarity of this stunning endpoint detection and response software image, available in high resolution for all your screens.

Captivating Endpoint Detection And Response Software Image Art
Immerse yourself in the stunning details of this beautiful endpoint detection and response software wallpaper, designed for a captivating visual experience.

Detailed Endpoint Detection And Response Software Landscape Concept
Discover an amazing endpoint detection and response software background image, ideal for personalizing your devices with vibrant colors and intricate designs.
Breathtaking Endpoint Detection And Response Software Image for Desktop
Discover an amazing endpoint detection and response software background image, ideal for personalizing your devices with vibrant colors and intricate designs.

Artistic Endpoint Detection And Response Software Image Illustration
Immerse yourself in the stunning details of this beautiful endpoint detection and response software wallpaper, designed for a captivating visual experience.
.jpg)
Mesmerizing Endpoint Detection And Response Software Artwork Concept
Experience the crisp clarity of this stunning endpoint detection and response software image, available in high resolution for all your screens.
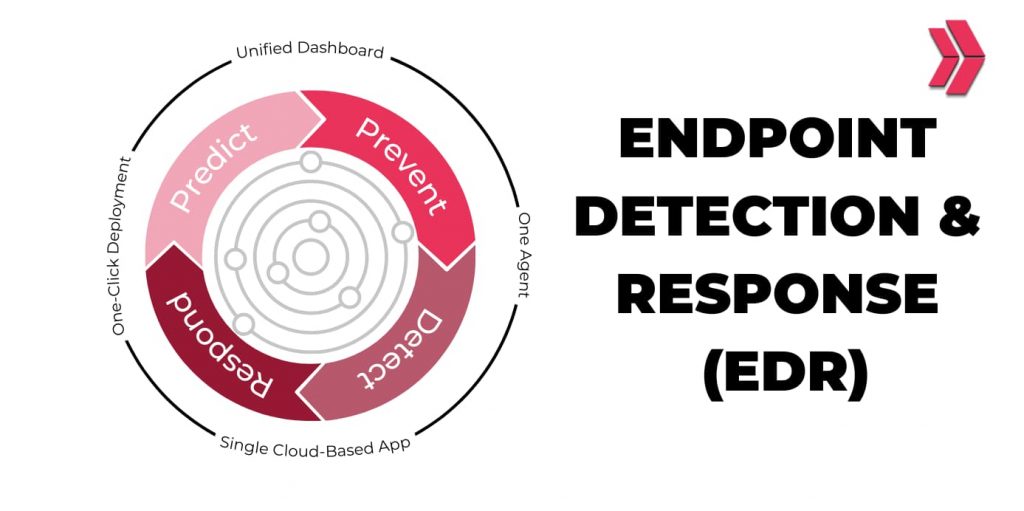

0 Response to "Endpoint Detection And Response Software"
Post a Comment